A long-standing vulnerability unearthed in the GNU Bash software, nicknamed Shellshock, has disrupted the daily activities of the Linux system administrator community, as Linux distributors, cloud vendors and end users grapple to understand the full scope of the potential damage it could cause.
"It's a very subtle and complicated vulnerability," said Owen Garrett, head of products for Nginx, a provider of server software.
The vulnerability "is trivially easy to exploit if you know what you are doing, so it really is a potentially serious problem," Garret said. "The upside is that the remedy is quick and easy."
The vulnerability is a flaw in the open-source GNU Bash shell found in nearly all Linux distributions, as well as in the Apple OS X operating system.
Thursday, researchers found a second, related vulnerability in the shell.
A shell is an interface for users to interact with computers, by way of either a graphical environment interface or -- in Bash's case -- a text-based command line interface. The vulnerability allows a malicious user to issue commands to the operating system.
In one sense, the vulnerability is not a serious one, noted Wolfgang Kandek, chief technology officer of IT security firm Qualys. A user with access to Bash already can access all the commands that the operating system offers to routine users. But it can be dangerous insofar as Bash is also used by other programs to complete their own tasks, and thus may offer a backdoor into some systems.
For instance, it could be used with the CGI (Common Gateway Interface), Kandek noted. CGI is a legacy, but still widely used, technology used in the early days of the commercial Internet to provide user interactivity to websites. CGI uses Bash to manipulate the server's OS.
A malicious user could inject commands into a CGI request that would get processed by the server, Kandek said. An attacker, for instance, could use Shellshock to take advantage of some other vulnerability that could not otherwise be executed from over the network, perhaps a vulnerability that would allow the attacker to then gain control of the machine.
Administrators are encouraged to patch their systems as quickly as possible. This is the easy part. In most Linux distributions, updating the system software can usually be done through a single command, Kandek said.
Fortunately, all the major Linux vendors quickly issued patches, including Debian, Ubuntu, Suse and Red Hat.
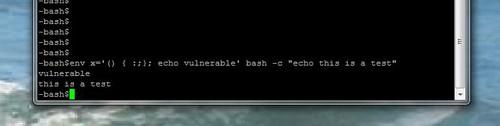
Red Hat also posted a one-line command that could easily test if a machine is vulnerable to the attack.
And not a second too soon, given that software programs that exploit the vulnerability quickly surfaced after the news of the vulnerability broke.
Running a honeypot server, IT management firm AlienVault has also found that multiple parties are already scanning the Internet to find machines with the vulnerability.
A honeypot is a machine placed on the Internet with the intent to characterize how much and what kind of malicious activity is taking place online, usually by using unpatched software that attackers can use to gain access.
Cloud infrastructure services providers that offer stock Linux distributions as virtual images, which are used based on the latest stock release of a distribution, could have unpatched versions of Bash. Some may have already mitigated the issue: Amazon Web Services, which maintains its own version of Linux, automatically updates any Linux virtual machines with the latest patches before they are deployed.
As a general best practice, however, anyone deploying a virtual machine for the first time should immediately update the software, Kandek said.
Joab Jackson covers enterprise software and general technology breaking news for The IDG News Service. Follow Joab on Twitter at @Joab_Jackson. Joab's e-mail address is Joab_Jackson@idg.com